
Privacy-Focused Web Development: Building GDPR, CCPA, and AI-Regulation Compliant Sites
The Imperative of Privacy in the Modern Digital Ecosystem As we live in the age of the information era, information can be harnessed like a
no CommentsBrief us your requirements below, and let's connect
1101 - 11th Floor
JMD Megapolis, Sector-48
Gurgaon, Delhi NCR - India
1st floor, Urmi Corporate Park
Solaris (D) Opp. L&T Gate No.6
Powai, Mumbai- 400072
#12, 100 Feet Road
Banaswadi,
Bangalore 5600432
UL CyberPark (SEZ)
Nellikode (PO)
Kerala, India - 673 016.
Westhill, Kozhikode
Kerala - 673005
India

The Imperative of Privacy in the Modern Digital Ecosystem As we live in the age of the information era, information can be harnessed like a
no Comments
Introduction Security of web applications is a hot topic because once an intruder gains access to an application, it becomes a breeding ground for their
no Comments
In the modern world, cyber-security is becoming a real challenge, as government institutions, giant companies, and persons are acutely suffering due to cyber-attacks. The truth
no Comments
An encrypted virus is a computer malware that’s become a serious threat to global businesses in the last half-decade. An encrypted virus is defined as
no Comments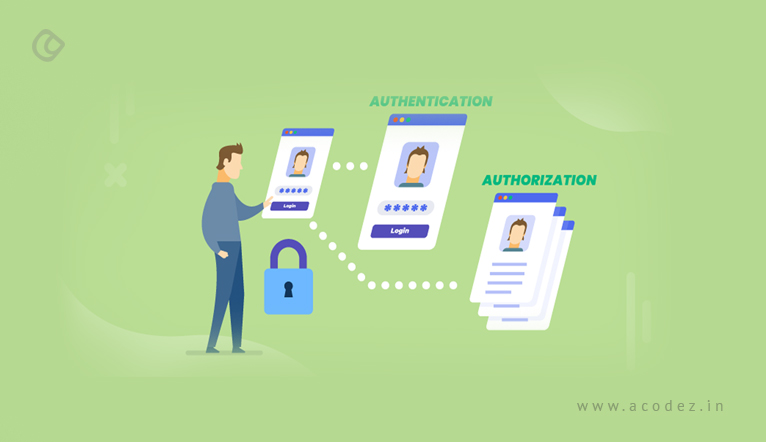
Authentication is defined as a process/procedure/methodology of confirming the identity of a user. In layperson’s definition, it is a method of confirming whether the person
no Comments
HSMs are primarily focused on security but they also need to be fast. Crypto operations are very demanding operations and require important processing power. Crypto
no Comments
Sending and receiving of emails have been an ordinary way of communication between people, learning instructions, companies, non-profit making institutions, et al. Anyone can send
no Comments
Today, the majority of internet users have created scores of accounts online, and the high chances are most of them are reusing the same password
no Comments
Digital marketing is an important part of every business. However, there is a challenge when a business has to share data that should be kept
no Comments
In this blog, we will detail how modern banking can be viewed in terms of three fundamental concepts: the businesses, the infrastructure, and open banking.
no Comments
Severe competition and increasingly volatile markets push CIOs and CISOs to rethink their IT and bring costs down. At the same time, many banks opt
no Comments
Today, crypto-operations are becoming an extraordinarily important asset for modern banking and modern financial institutions in general. To secure these crypto-operations, HSMs are fundamental. But
no Comments
The term social engineering covers an extensive list of malicious activities that are executed through human interrelations. It plays around with psychology manipulations of innocent
no Comments
There’s an ongoing discussion about the scarcity of skills within the cyber-security industry. The present cyber-security workforce is estimated to be 2.8 million and the
no Comments
Mobile devices, particularly smartphones that have features similar to computers are carried everywhere in purses, pockets, or cars. Besides their popularity, these devices are characterized
no Comments
The actual ongoing pandemic named “COVID-19” has dramatically raised the whole world about the existence of viruses that are deadly for humankind. COVID-19, created by
no Comments
Post-Quantum Crypto Post-Quantum crypto refers to a class of cryptographic algorithms and methods that are deemed to resist Quantum Computing attacks. Quantum computing uses quantum
no Comments
Very few people actually know exactly what is EMV and what it’s exactly related to. Putting it simply, EMV is everything – or almost everything
no Comments
With the current state of COVID-19 which has become a global threat to human existence on earth, one of the key measures to tackle the
one Comment
Social networks like Facebook, Twitter, Pastebin, et al. connect us with our family, colleagues, schoolmates, business partners, and customers, and even absolute uncos. Everyone enjoys
one Comment
Cyber-crime is described as criminal activity executed using a computer or the web directed at computers or an ICT system. It is a criminal act
no Comments
Just like the integration of electricity and the Internet of Things (IoT), a combination of machine learning (ML) with blockchain technology has the capability of
no Comments
In this article, we explain how compromising the PIN of a customer’s prepaid debit card may lead to catastrophic losses for a bank and why
no Comments
Businesses, regardless of their sizes worldwide are seeking methods to improve their efficacy and profitability by all means from their general activities to IT and
no Comments
With organisations needing data for various purposes, maintaining and setting a proper system or software for data protection have also become essential. The purposes can
no Comments